Manipulation of Data through Burp Suite’s Proxy
- KevinsinghJ
- Feb 15
- 4 min read
Burp Suite is a popular integrated platform used for web application security testing. It is widely employed by security professionals, penetration testers and ethical hackers to identify vulnerabilities in web applications. Developed by PortSwigger, Burp Suite offers a range of tools that facilitate various aspects of security testing, from mapping an application to exploiting its vulnerabilities.
At its heart, Burp Suite is designed to test how a web application interacts with its users. It achieves this by intercepting and analyzing HTTP/HTTPS requests and responses, enabling users to manipulate data and observe how the application behaves.
The main component and features of Burp Suite would be Proxy, Intruder, Repeater, Decoder, Comparer etc, as shown in below screenshot (I’m running the Burp Suite community edition)
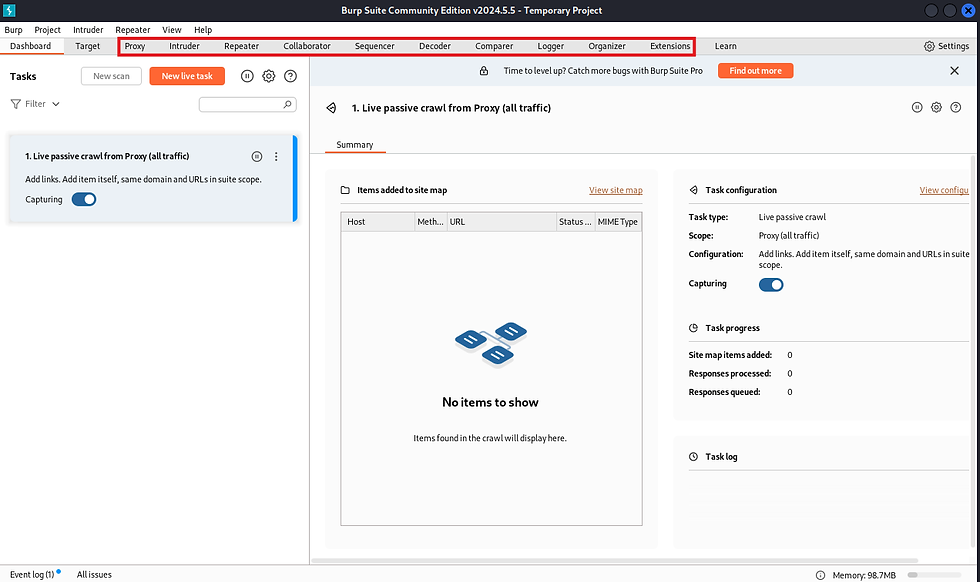
Dashboard View
Setting it Up
Today, I’ll just be discussing the proxy feature in Burp Suite, which is more than enough for beginners of this tool. Basically Burp Suite is like a proxy, so we’ll have to configure the proxy and divert the entire traffic, for example a client request should not go to the server directly and it has to go through this proxy
To begin, on the Burp Suite tool, click on Proxy → Proxy Settings to ensure the port which is set, in my case it’s the local host port 8080. It’s the Proxy Listeners, which means the entire proxy will listen to the request of the client through port 8080.

Same settings has to be applied on the browser, in my case it’s firefox. I can do so by going to the Settings → General → Network Settings (scroll all the way, it’s the last option under General). Once in Network Settings, by default No Proxy is chosen, we got to choose Manual Proxy Configuration (HTTP Proxy: localhost & Port: 8080). Click on OK once done.

We would also need to download one certificate, from http://burpsuite. Click on CA Certificate to get it downloaded.

Once the certificate is downloaded, head over to the browser’s Settings → Privacy & Security → Certificates → View Certificates → Authorities and click on Import (choose the certificate we downloaded), and click on OK
Relaunching the browser is advised to ensure the changes take effect accordingly.
Data Manipulation
Now, let me show the scenario where we’ll be doing the manipulation of data. To begin, head over to below link:-
Click on Login on the top right, and I'm pretty sure most of the readers here would not be having an account, hence kindly click on Create Account
Once that’s clicked, below page will appear, key-in your email ID to continue with the registration

And then below email will be sent to the email address, to complete the registration. Just click on the link to get it done.

You’ll be asked to input your name and then the page will redirect where your password is shown to login. Get the password saved in a notepad or elsewhere. Login with the email and that password (you can get the password changed to your preferred one once the login is successful)
Once it’s done, go over to the same link as given earlier, shown below again:-
This time it’ll be shown that you’re logged-in, click on Access the Lab

A shopping application will be shown where we’ll begin our demo of data manipulation. Before we can do that, click on My Account on top right and login with a dummy account (with below username and password)
Username: wiener
Password: peter
And then key-in your email and click on Update email. Then click on Home
The same shopping application will be shown but this time with you logged in. Click on the first item shown which is a leather jacket

Please note that the price shown for this jacket is $1337.00

Now, for our demo, we’ll get the price changed through Burp Suite. Before clicking on Add to Cart, head over to Burp Suite. Under proxy, click on Intercept is Off and notice that it’ll be shown as Intercept is On

Once that’s done, you can add the jacket to the cart on the browser. You’ll notice that it’ll just keep loading, because it’s not sent to the server, instead it’s intercepted by Burp Suite
Over in Burp Suite, this is what you’ll see with the price of $1337.00 (shown as 133700)

I changed the price to $10.00 (shown as 1000) and then i got to click on Forward to get it sent to the server. Then click on turn off the Intercept by clicking on Intercept is On

Once above is done, on the shopping application, you’ll notice that the cart has 1 item added. Simply click on it and see that the price has changed to what we wanted.
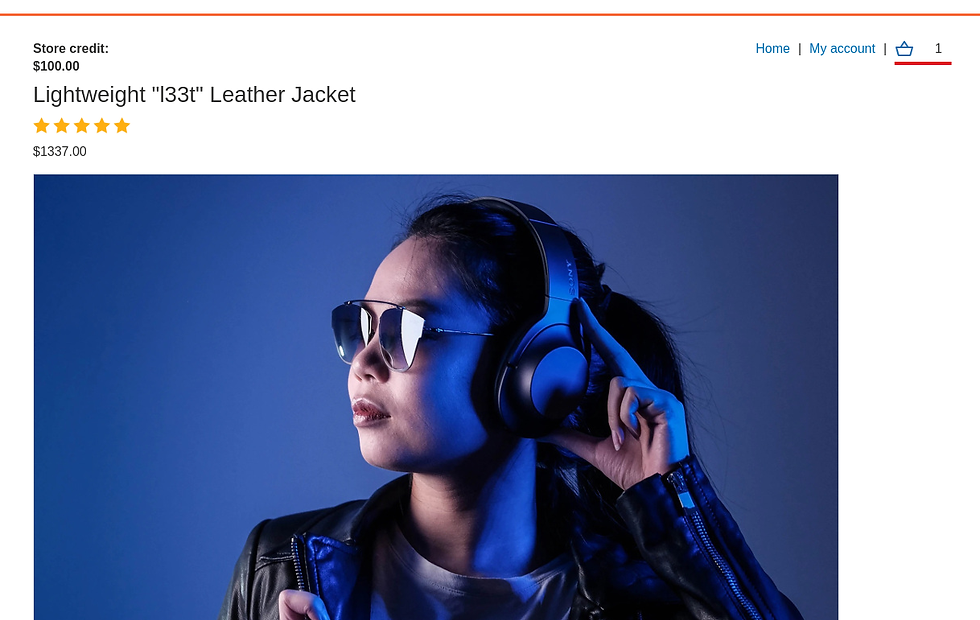

So basically we’ve successfully amended the price. It’s because there’s a huge security issue on this app (this is just a dummy application). It’s solely for learning purpose.